Firewalls and Internet security are crucial cybersecurity layers. A firewall is a specific tool that acts as a filter or barrier between your internal network and the outside internet, blocking
unauthorized traffic. Internet security is the broader strategy that uses firewalls, alongside antivirus, user policies, and encryption, to protect all online activity and data.
As a certified network security professional who has spent the last decade in the trenches fighting cyber threats, I’ve seen firsthand what happens when defenses fail. Understanding how to properly configure firewalls and internet security is not just a technical best practice—it’s essential for survival in today’s threat landscape.
With sophisticated attacks now automated and targeting everyone from individuals to Fortune 500 companies, a single misconfiguration can lead to a catastrophic breach.
This guide leaves the theory behind and focuses on actionable insights. Here’s exactly what we will cover:
-
How Firewalls Think: The core mechanics behind traffic analysis and rule enforcement.
-
The Right Tool for the Job: Comparing key firewall types (NGFW, Cloud, etc.) for different scenarios.
-
Strategy is Key: How to integrate your firewall into a resilient, layered defense strategy.
-
Future-Proofing Your Defenses: The impact of emerging trends like SASE and AI.
What Are Firewalls?
Firewalls and Internet Security are inseparable in any modern cybersecurity strategy. A firewall is a critical network security system that works as a barrier between trusted internal networks and untrusted external networks like the internet. Instead of letting all traffic flow freely, it filters data packets, blocks malicious requests, and ensures secure communication.
For readers who want a dedicated breakdown of firewall basics, check out our full guide on What is a Firewall.
Definition and Core Purpose
At its simplest, a firewall can be:
-
Hardware-based (dedicated network appliances).
-
Software-based (installed on individual devices).
-
Hybrid models combining both.
Its main goal is to block unauthorized access and enforce organizational security policies. Think of it as a gatekeeper standing at the edge of your network—deciding which traffic is safe and which must be rejected.
Brief History and Evolution of Firewalls
The concept of firewalls dates back to the late 1980s, evolving significantly as cyber threats have grown more complex. Early firewalls focused solely on filtering packets by IP address and port, offering basic protections.
| Year | Milestone |
|---|---|
| 1987 | Packet-Filtering Firewalls introduced |
| 1993 | Stateful Inspection Firewalls |
| 1997 | Proxy Firewalls with application-layer filtering |
| 2010s | Next-Generation Firewalls (NGFW) with intrusion prevention |
| 2020s | Cloud-based and virtual firewalls gain traction |
This timeline shows how firewalls have moved from simple packet filters to essential components in Firewalls and Internet Security frameworks across enterprises and cloud environments.
Firewalls and Internet Security: Definition and Importance
Firewalls and Internet Security are the backbone of digital defense in 2025. While a firewall provides the first layer of protection, internet security represents the broader set of practices and tools that keep users, devices, and data safe from online threats.
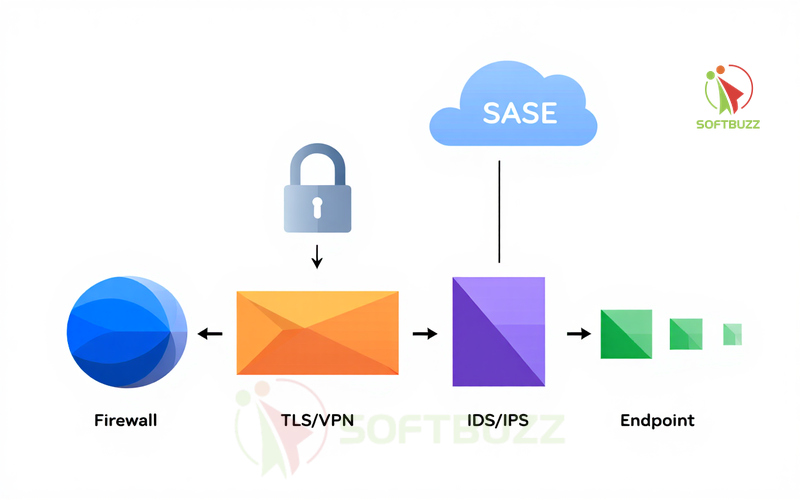
Definition and Components
Internet security is more than a single technology—it’s a multi-layered strategy. A strong Firewalls and Internet Security framework typically includes:
-
Endpoint security: Antivirus and anti-malware software.
-
Network security: Firewalls, IDS/IPS to monitor and block malicious traffic.
-
Data encryption: TLS and VPN protocols that secure data in transit.
-
Access management: Multi-factor authentication and identity controls.
-
User awareness: Training to reduce human error in cybersecurity.
Each component works together to reduce risks like phishing, ransomware, and zero-day attacks. According to the NIST Cybersecurity Framework, building multiple layers of security is the recommended best practice for enterprises and individuals alike.
Relationship Between Firewalls and Internet Security
Think of Firewalls and Internet Security as a shield: the firewall is the outer gatekeeper filtering obvious threats, while internet security layers—encryption, antivirus, and access policies—offer deeper protection.
This defense-in-depth approach ensures that even if a firewall is misconfigured, other layers still safeguard the system. As noted by Gartner, organizations adopting layered defenses that combine firewalls, endpoint protection, and Zero Trust models reduce breach risks by up to 50%.
For both businesses and individuals, adopting Firewalls and Internet Security together is no longer optional—it’s essential for survival in today’s evolving threat landscape. To explore the fundamentals, see our detailed guide: What is a Firewall.
How Firewalls Work to Protect Users and Organizations
Firewalls and Internet Security are most effective when you understand how firewalls actually operate. At their core, firewalls continuously monitor, filter, and block network traffic, acting as intelligent gatekeepers that distinguish safe connections from malicious ones.
Basic Principles (Monitoring, Filtering, Blocking)
Firewalls evaluate data packets based on rules like source/destination IP, ports, and protocols. They block unauthorized or suspicious traffic while allowing legitimate communication. Advanced solutions add deep packet inspection (DPI) to detect hidden threats. According to the NIST Cybersecurity Framework, monitoring and filtering at this level are critical to modern Firewalls and Internet Security strategies.
Inbound vs. Outbound Protection
-
Inbound protection: Prevents attackers from exploiting internal systems by blocking malicious requests.
-
Outbound filtering: Stops unauthorized data exfiltration or botnet connections leaving the network.
Both layers are essential for Firewalls and Internet Security, ensuring that organizations defend against intrusions while also controlling sensitive data leaving their environment.
Placement in Network Architecture
Firewalls can be deployed in multiple layers of an IT ecosystem:
-
Network perimeter (edge firewalls): Installed at the boundary between the internal network and the internet.
-
Cloud environments: Virtual firewalls integrated into cloud platforms for workloads and SaaS protection.
-
Endpoints: Host-based firewalls running on individual devices to monitor local traffic.
This layered deployment model is recommended by Gartner as part of a defense-in-depth approach, making Firewalls and Internet Security more resilient against complex attack vectors.
Types of Firewalls and Their Roles in Internet Security
Different types of firewalls serve distinct roles within Firewalls and Internet Security. Choosing the right one depends on network size, complexity, and risk tolerance.
Common Firewall Types
Each firewall type offers unique strengths and weaknesses. From packet filtering in small networks to NGFWs in enterprises, combining them ensures stronger Firewalls and Internet Security.
| Firewall Type | Best Use Cases | Advantages | Limitations |
|---|---|---|---|
| Packet-Filtering | Small networks, simple setups | Fast, low resource use | Limited context, easily bypassed |
| Stateful Inspection | Enterprises needing stronger control | Tracks connection state, improved accuracy | Higher resource consumption, complex rules |
| Proxy / Application Firewalls | Web & app traffic filtering | Deep packet inspection, hides internal IPs | Adds latency, complex setup |
| Next-Generation Firewalls (NGFW) | Large enterprises, cloud adoption | Integrated IPS, TLS inspection, app awareness | Expensive, requires skilled management |
| Host-Based Firewalls | Endpoint and device-level protection | Customizable per user/device | Dependent on endpoint health |
| Network-Based Firewalls | Perimeter defense for organizations | Centralized visibility, broad coverage | Can miss internal threats |
| Cloud / Virtual Firewalls | Remote workforces, SaaS/IaaS security | Scalable, API integration | Reliant on provider infrastructure |
Practical Example
A remote workforce accessing SaaS and IaaS platforms benefits most from cloud-based firewalls, which scale dynamically and integrate with cloud APIs for seamless control.
Why This Matters for Firewalls and Internet Security
According to Gartner, more than 70% of enterprises in 2025 will deploy Next-Generation Firewalls or cloud-native solutions to support distributed workforces. This shows that no single firewall is enough—Firewalls and Internet Security must be layered, combining perimeter, endpoint, and cloud controls for full protection.
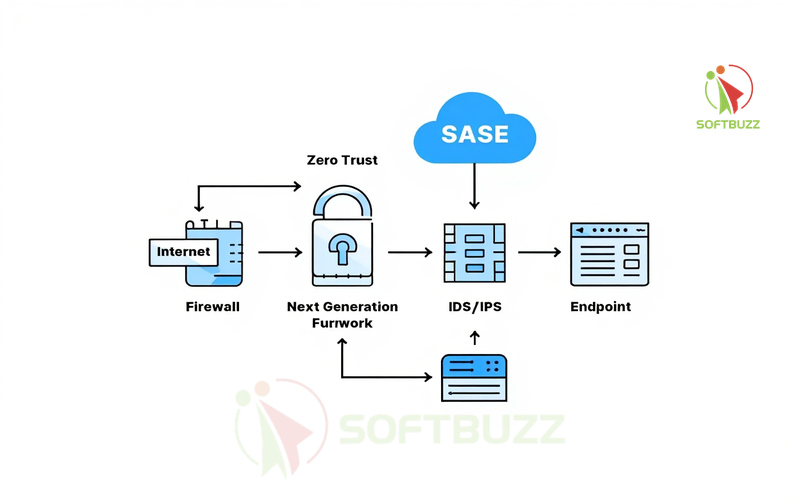
The Essential Role of Firewalls in Modern Internet Security
Firewalls and Internet Security work best as part of a layered defense strategy, protecting against diverse threats but never as a standalone solution.
While firewalls are crucial in building a secure network perimeter, relying on them alone is insufficient. Modern attackers exploit multiple vectors that firewalls cannot always stop—such as social engineering, phishing, or zero-day vulnerabilities.
Defense-in-Depth Approach
Defense-in-depth is the principle of layering multiple security measures to cover the weaknesses of any single tool. Within Firewalls and Internet Security, this means combining:
-
Endpoint protection (antivirus, EDR solutions).
-
Encryption protocols to secure data in transit.
-
Intrusion detection/prevention systems (IDS/IPS).
-
Continuous monitoring and logging to identify anomalies.
According to the NIST Cybersecurity Framework, firewalls are only one element of a comprehensive defense strategy.
Deployment in Different Scenarios
Firewalls and Internet Security look different depending on context—from basic home routers to NGFWs in enterprises and cloud-native SASE models.
-
Home users: Rely on router or OS-level firewalls for everyday protection.
-
SMBs: Need hybrid hardware/software firewalls with updated rules and endpoint defenses.
-
Enterprises: Use Next-Generation Firewalls (NGFWs), segmented networks, and threat intelligence.
-
Cloud environments: Adopt virtual firewalls and SASE (Secure Access Service Edge) for distributed teams.
Why Firewalls Must Be Integrated
Firewalls and Internet Security must be combined with Zero Trust, endpoint protection, and AI-driven monitoring for maximum effectiveness.
Gartner reports that enterprises using layered defenses—firewalls plus Zero Trust and continuous monitoring—reduce breach risks by over 50%. This confirms that Firewalls and Internet Security must always be part of a multi-layered defense model, not the sole line of defense. For more practical tips, explore our computer tricks guide on security best practices.
Firewalls vs. Common Internet Threats
Firewalls and Internet Security stop many common attacks, but some advanced threats still bypass them—making layered defense essential.
Firewalls are powerful against several classes of cyber threats but have well-known limitations. They excel at blocking unauthorized access and malicious traffic, yet cannot fully prevent phishing, insider threats, or zero-day exploits.
Threats Firewalls Can Mitigate
Firewalls and Internet Security protect against unauthorized access, basic malware spread, and denial-of-service attacks.
Typical threats firewalls can block include:
-
Unauthorized access attempts.
-
Basic malware propagation through open ports.
-
Denial of Service (DoS) attacks at the network edge.
-
Port scanning and reconnaissance activities.
These protections form the first layer of Firewalls and Internet Security, reducing risks before they reach internal systems.
Threats Firewalls Cannot Fully Stop
Some cyber threats bypass Firewalls and Internet Security, including phishing, insider risks, and advanced persistent threats.
Limitations include:
-
Phishing attacks that rely on human error.
-
Malware in encrypted channels, unless deep inspection is used.
-
Insider threats and social engineering tactics.
-
Advanced persistent threats (APTs) exploiting stealth and zero-day vulnerabilities.
This is why Firewalls and Internet Security must integrate with endpoint defenses, user training, and monitoring.
Coverable vs. Non-Coverable Threats
Firewalls and Internet Security are strong against packet intrusions but weak against social engineering and credential theft.
| Coverable Threats by Firewall | Non-Coverable Threats |
|---|---|
| Packet-based intrusions | Human-based social engineering |
| Network scanning | Zero-day exploits without signatures |
| Basic DoS attacks | Credential theft |
Real-World Example
The WannaCry ransomware outbreak in 2017 proved that Firewalls and Internet Security alone cannot stop unpatched vulnerabilities.
WannaCry spread globally by exploiting unpatched systems—even those behind firewalls. This highlighted the need for patch management, endpoint protection, and layered defense in conjunction with firewalls. According to NIST, patching and continuous monitoring are as critical as firewalls themselves in any resilient security program.
Integrating Firewalls into a Comprehensive Security Strategy
Firewalls and Internet Security are most effective when combined with other tools, best practices, and compliance standards for layered protection.
Firewalls alone cannot provide complete protection. Their peak effectiveness comes when integrated with complementary technologies, strict rule management, and regulatory compliance.
Complementary Technologies
Pairing Firewalls and Internet Security with IPS, antivirus, VPNs, and Zero Trust creates a multi-layered shield against threats.
-
Intrusion Prevention Systems (IPS): Detect and block malicious activity missed by firewalls.
-
Antivirus (AV): Protects endpoints from malware and viruses.
-
VPNs: Encrypt traffic and secure remote connections.
-
Zero Trust frameworks: Assume no implicit trust, verifying every request.
Together, these extend Firewalls and Internet Security beyond the perimeter, covering endpoints, users, and encrypted traffic.
Firewall Rules Management & Best Practices
Regularly updating firewall rules is essential to keep Firewalls and Internet Security strong against evolving threats.
Best practices include:
-
Frequent rule reviews and updates to avoid misconfigurations.
-
Log monitoring and audits to detect anomalies.
-
User training to minimize human error.
According to the CIS Controls and NIST guidelines, ongoing audits are critical to reduce vulnerabilities while ensuring firewalls remain effective.
Compliance and Privacy Considerations
Firewalls and Internet Security must comply with frameworks like GDPR and HIPAA to balance data protection with operational needs.
Key points:
-
Configure firewalls to respect data privacy policies.
-
Ensure logging and monitoring meet compliance standards.
-
Document firewall changes for audit readiness.
Following frameworks such as NIST and CIS Controls ensures firewall configurations are both secure and adaptable, aligning with global regulations.
Choosing and Deploying Firewalls: Guidelines for 2025
Firewalls and Internet Security must be chosen based on network needs, scalability, and deployment strategy to stay resilient in 2025.
Selecting the right firewall solution requires careful assessment of organizational size, traffic volume, cloud integration, and available IT skills. A poor fit can leave critical gaps in Firewalls and Internet Security.
Key Selection Criteria
Choosing a firewall depends on network size, cloud usage, and the expertise available to manage Firewalls and Internet Security.
-
Network size and complexity: Larger networks require NGFWs or cloud-native firewalls.
-
Traffic types: Application-heavy traffic benefits from DPI and TLS inspection.
-
Cloud integration: SaaS/IaaS adoption favors virtual or API-driven firewalls.
-
Skill availability: Complex setups need in-house or external expertise.
Purchase vs. Open-Source vs. Managed Options
Firewalls and Internet Security can be commercial, open-source, or managed—each with trade-offs in cost, features, and control.
-
Commercial firewalls: Vendor support, advanced features, and easier scaling.
-
Open-source: Flexible and customizable, but require skilled management.
-
Managed firewalls: Outsourced to providers, reducing operational burden but limiting direct control.
Implementation Checklist
Snippet: A structured rollout ensures Firewalls and Internet Security are effective from day one.
Steps to follow:
-
Define security policies aligned with organizational goals.
-
Conduct network assessments to identify vulnerabilities.
-
Deploy firewall hardware/software based on requirements.
-
Test rule effectiveness and make iterative adjustments.
-
Establish continuous monitoring and updates.
Using a comparison matrix that includes application awareness, logging, and auto-updates helps decision-makers choose the right solution in the 2025 security landscape.
The Future of Firewalls and Internet Security
Firewalls and Internet Security in 2025 will evolve with AI, SASE, and adaptive defenses to meet new cyber threats.
Emerging technologies are reshaping firewall deployment and capabilities. The future of Firewalls and Internet Security depends on adapting to automation, cloud delivery, and ever-changing threats.
AI, Machine Learning, and Automation
AI-driven Firewalls and Internet Security enable predictive detection and automated response to fast-moving threats.
These technologies allow real-time rule adjustments, anomaly detection, and automated containment of suspicious activity.
The Rise of SASE and Cloud-Native Approaches
Firewalls and Internet Security are shifting to cloud-native SASE, combining networking and security in one platform.
SASE reduces latency and enhances flexibility for remote and hybrid workforces, making it a cornerstone of modern architecture.
Emergent Threats and Adaptability
Firewalls and Internet Security must scale with IoT and defend against increasingly sophisticated attacks.
The rapid growth of IoT devices and complex attack vectors requires firewalls that are adaptable, scalable, and cloud-ready.
According to Gartner and Forrester, AI-powered NGFWs and cloud-native firewalls will dominate by 2025, becoming critical investments for long-term resilience.
Frequently Asked Questions: Firewalls and Internet Security
Here are the top questions users ask about Firewalls and Internet Security, from malware protection to firewall rules and modern security practices.
Q1: Can firewalls stop all malware?
A: Firewalls can block malware transmitted through network traffic, but they cannot detect malicious files from USB drives or hidden inside encrypted traffic. For effective Firewalls and Internet Security, they must be paired with endpoint protection and anti-malware tools.
Q2: Is a firewall better than antivirus?
A: No. Firewalls regulate network access, while antivirus removes malicious files on endpoints. Both serve different roles, and combining them is essential for comprehensive Firewalls and Internet Security.
Q3: Do I need both hardware and software firewalls?
A: Yes, ideally. Hardware firewalls defend the network perimeter, while software firewalls (host-based) protect individual devices. Together, they create layered Firewalls and Internet Security against both external and internal threats.
Q4: How often should firewall rules be updated?
A: Best practice is to review and update firewall rules quarterly or after vulnerabilities, network changes, or incidents. According to NIST and CIS Controls, regular audits keep Firewalls and Internet Security effective and compliant.
Q5: Can firewalls prevent phishing attacks?
A: No. Firewalls cannot stop phishing emails or fake websites that trick users into revealing credentials. Defense requires email filters, user training, and multi-factor authentication alongside Firewalls and Internet Security.
Q6: What’s the difference between NGFW and traditional firewalls?
A: Next-Generation Firewalls (NGFWs) combine packet filtering with intrusion prevention, TLS inspection, and app awareness. They are more advanced than traditional firewalls and a core part of enterprise Firewalls and Internet Security in 2025 (Gartner).
Q7: Do home users need a firewall?
A: Yes. Even basic router or OS-level firewalls protect against unauthorized access attempts. For safer Firewalls and Internet Security, home users should also enable antivirus and keep systems patched.
Q8: Will firewalls adapt to future threats like IoT and AI-driven attacks?
A: Yes. Modern Firewalls and Internet Security already integrate AI for predictive detection and automation. According to Forrester, cloud-native and AI-powered NGFWs will be critical to secure IoT-heavy environments.
Glossary of Key Terms
This glossary explains the most important terms in Firewalls and Internet Security, from packets to Zero Trust and SASE.
-
Packet: A small unit of data transmitted over a network. Firewalls analyze packets to determine whether to allow or block traffic.
-
Port: A communication endpoint in networking used by protocols. Attackers often scan ports, making them critical in Firewalls and Internet Security.
-
DMZ (Demilitarized Zone): A network segment acting as a buffer zone between an internal network and untrusted external networks like the internet.
-
DPI (Deep Packet Inspection): A technique that examines packet content beyond headers to detect threats, often used in NGFWs.
-
Zero Trust: A security model assuming no implicit trust and requiring verification of every access request. Recommended by NIST for modern enterprise defense.
-
NGFW (Next-Generation Firewall): An advanced firewall integrating intrusion prevention (IPS), application awareness, and threat intelligence—now a core element of enterprise Firewalls and Internet Security.
-
SASE (Secure Access Service Edge): A cloud-delivered architecture that merges WAN and security controls. According to Gartner, SASE adoption is accelerating as organizations move to hybrid and remote work.
Conclusion
Firewalls and Internet Security remain the foundation of digital defense in 2025. Their value is maximized when combined with endpoint protection, encryption, and continuous monitoring, rather than being used in isolation.
To recap, strong Firewalls and Internet Security requires:
-
Choosing the right firewall type (packet-filtering, NGFW, cloud-native).
-
Deploying firewalls according to context: home, SMBs, enterprises, cloud.
-
Managing firewall rules and updating configurations regularly.
-
Integrating complementary tools like IPS, antivirus, and Zero Trust.
-
Aligning with frameworks such as NIST Cybersecurity Framework and CIS Controls.
-
Adapting to new technologies, from AI-driven detection to SASE models.
According to Gartner, organizations that integrate firewalls into layered defenses with Zero Trust and AI monitoring can reduce breach risks by over 50%. This proves that firewalls must evolve with modern threats to remain effective.
If you want to explore more on security and optimization, check out our guides at Softbuzz homepage or explore Computer Tricks for practical tips.
Question for you: What type of firewall do you currently use, and do you feel it’s enough to protect you in today’s threat landscape?