In today’s digital age, where everything from banking to social media relies on internet connectivity, protecting your network is no longer optional—it’s essential. Yet, many users still ask, what is a firewall, and why does it matter?
A firewall is often your network’s first line of defense against hackers, malware, and unauthorized access. Whether you’re managing a corporate infrastructure or simply browsing from home, understanding how firewalls work can dramatically improve your online security. From personal experience, learning about firewalls helped me secure my devices and assist others in building stronger, more resilient networks.
1. What is a Firewall?
A firewall is a security system—either hardware-based, software-based, or a combination of both—that serves as a digital barrier between your private network and the broader internet or any untrusted network. Its main job is to monitor, filter, and control network traffic based on pre-established security rules.
Think of a firewall like a security guard standing at the entrance of your network. It checks every “packet” of data trying to get in or out. If the packet comes from a trusted source and follows the rules, it’s allowed through. If not, it’s blocked.
Key Concept: The Gatekeeper of the Internet
Most internet users don’t realize how often they rely on firewalls. Every time you connect to public Wi-Fi or browse from your office network, a firewall is working behind the scenes—either on your router, computer, or managed by your service provider—to protect your data from intrusions.
Example From Experience:
When I started managing a small coworking space, we initially had no firewall protecting our internal network. Within weeks, some of the devices started showing suspicious behavior—unauthorized remote access attempts, slow connections, and unusual file transfers. Once we installed a basic firewall and set strict rules, the problems nearly vanished. The difference was night and day.
Why It Matters
Without a firewall, your network is like an unlocked door in a busy neighborhood—anyone can walk in. With a firewall in place, you set boundaries, control who can communicate with your devices, and monitor for potential threats in real time.
Whether you’re a home user just trying to protect your smart TV and phone, or a system administrator securing a corporate intranet, understanding what a firewall is gives you the foundation to defend your digital perimeter effectively.
2. How Does a Firewall Work?
Firewalls operate by inspecting network traffic and enforcing security policies. They analyze data packets—units of communication over a digital network—and determine whether to allow or block them based on established rules.
Key functions include:
- Packet Filtering: Examines packets and blocks those that don’t match security criteria.
- Stateful Inspection: Tracks active connections to determine which packets are safe.
- Proxy Services: Acts as a middleman to prevent direct contact between networks.
- Deep Packet Inspection: Analyzes the content of packets to identify sophisticated threats.
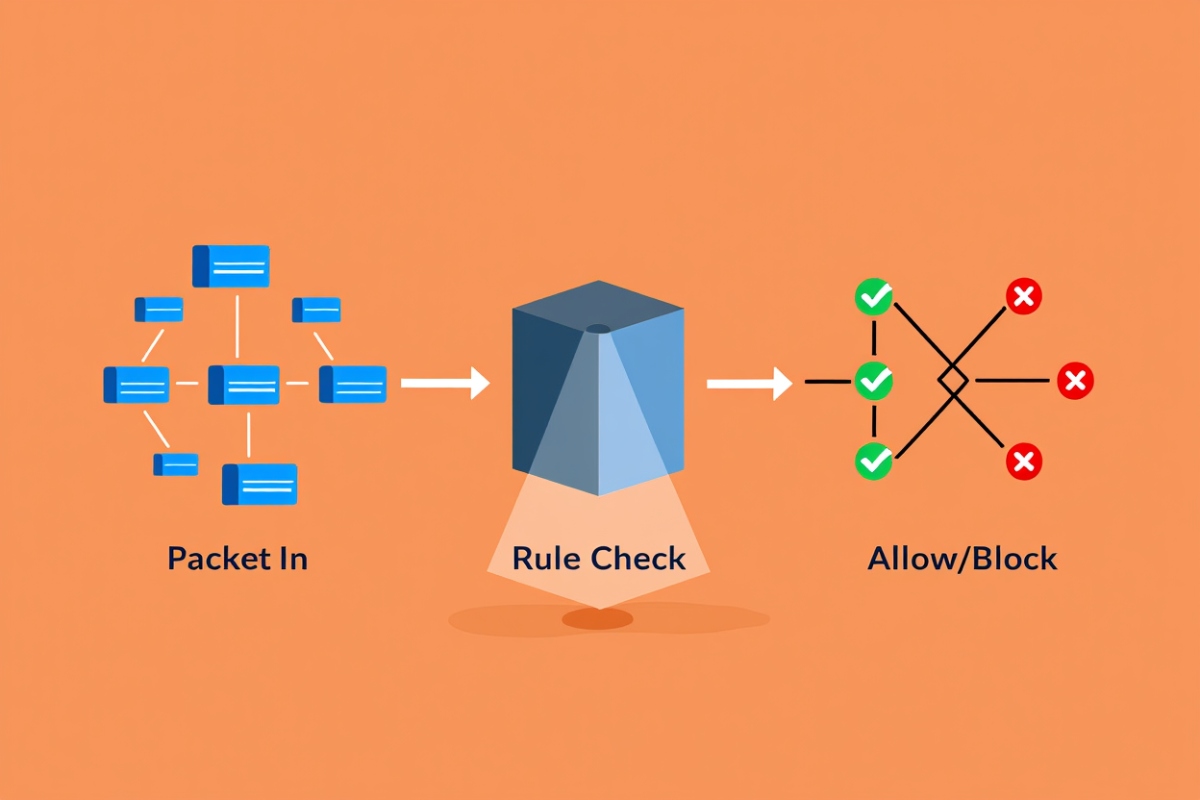
In my professional experience, configuring a firewall with deep packet inspection significantly reduced malware incidents across our small business network.
3. Types of Firewalls
There’s no one-size-fits-all solution when it comes to firewalls. Different environments—home, office, enterprise, cloud—require different tools. That’s why understanding the various types of firewalls is essential to choosing the right one for your needs.
Below are the five main categories, each with unique features and applications.
3.1. Packet-Filtering Firewalls
What it does: This is the most basic type of firewall. It inspects individual data packets and filters them based on predefined rules such as source/destination IP address, port number, and protocol.
Use Case: Lightweight environments or legacy systems where performance is more critical than deep inspection.
Pros:
- Low resource usage
- Fast processing
Cons:
- Doesn’t track connection state
- Limited visibility into packet contents
3.2. Stateful Inspection Firewalls
What it does: These firewalls monitor the state of active connections and make decisions based on both the packet’s contents and its relation to previous packets.
Use Case: Small to medium-sized businesses that need more control than basic filters provide.
Pros:
- Smarter filtering than packet-based
- Tracks active sessions
- More secure for internal networks
Cons:
- Requires more memory and processing power
- May struggle under heavy loads without optimization
3.3. Proxy Firewalls
What it does: A proxy firewall sits between internal users and the external internet, acting as an intermediary that filters traffic at the application layer (e.g., HTTP, FTP).
Use Case: Organizations requiring user-level content control, such as schools or companies enforcing browsing policies.
Pros:
- Deep content inspection
- Can cache content for performance
- Provides anonymity for internal users
Cons:
- Can slow down internet access if not optimized
- More complex to configure
3.4. Next-Generation Firewalls (NGFW)
What it does: NGFWs combine traditional firewall features with modern security tools like Intrusion Prevention Systems (IPS), antivirus scanning, URL filtering, and more—all in one platform.
Use Case: Enterprises or security-sensitive environments like healthcare or finance.
Pros:
- Comprehensive protection
- DPI (Deep Packet Inspection)
- Integrated with threat intelligence
Cons:
- Expensive and resource-heavy
- Requires expert configuration
3.5. Hardware vs. Software Firewalls
Hardware Firewalls:
- Standalone physical devices
- Best for protecting entire networks
Software Firewalls:
- Installed on individual devices
- Ideal for personal computers and mobile users
Summary Table
| Firewall Type | Best For | Security Depth | Performance Impact | Ease of Use |
|---|---|---|---|---|
| Packet-Filtering | Legacy or simple environments | Low | Minimal | Easy |
| Stateful Inspection | SMB networks | Medium | Moderate | Moderate |
| Proxy Firewall | Policy enforcement environments | High | High | Moderate |
| NGFW | Enterprise, cloud-first businesses | Very High | High | Complex |
| Software/Hardware Firewall | Personal use or full network edge | Varies | Varies | Varies |
Read more:
- What Is DNS Server? The Internet Shortcut You Never Knew You Needed
- What Is a VPN? A Complete Beginner’s Guide to Online Security
- What is LAN vs WAN? Key Differences Explained for Everyday Users
- What is Subnet Mask? A Beginner-Friendly Guide to IP Networks
4. Importance of Firewalls
Firewalls are not just optional add-ons—they are essential security components in every modern network. Whether you’re using a single laptop or managing hundreds of endpoints across an enterprise, firewalls provide critical protection on multiple levels.
Below are key reasons why firewalls are indispensable for personal and business cybersecurity:
4.1. Block Unauthorized Access
A firewall acts as a gatekeeper. It prevents outsiders—including hackers, bots, and malicious scripts—from accessing your internal network without permission. Without this barrier, attackers could exploit open ports or vulnerable services and gain entry.
4.2. Protect Sensitive Information
From credit card details to business contracts, sensitive data must be shielded from prying eyes. Firewalls help safeguard these assets by controlling who can access what—and from where.
- Encrypts or restricts outbound data leaks
- Prevents unauthorized file transfers
- Blocks spyware from sending stolen data
4.3. Prevent Malware and Viruses
Modern firewalls—especially Next-Gen Firewalls (NGFWs)—come with built-in malware and antivirus scanning. They inspect traffic in real time and detect known threats before they reach your system.
4.4. Control Employee or User Behavior
In organizational settings, firewalls can be used to enforce policies:
- Block access to distracting or risky websites (e.g., gambling, social media)
- Monitor which apps and services are used during work hours
- Restrict file uploads or unauthorized cloud backups
This not only improves security but boosts productivity.
4.5. Comply with Security Regulations
Industries like healthcare, finance, and education often require strict data protection standards (e.g., HIPAA, PCI-DSS, GDPR). Firewalls help ensure that your network complies with these regulations by:
- Enforcing encryption
- Limiting inbound and outbound access
- Generating security logs for audits
4.6. Maintain Network Performance and Uptime
Besides security, firewalls contribute to overall network health:
- Detect and block DDoS attacks before they crash servers
- Prioritize traffic to essential services
- Limit bandwidth abuse from non-essential applications
Firewalls don’t just block threats—they provide visibility, control, and peace of mind. For any modern digital environment, they’re as essential as locks are to your home.
5. Choosing the Right Firewall
Selecting the right firewall isn’t just about buying the most expensive one—it’s about finding the solution that fits your specific needs. From home users to enterprise architects, each environment requires a different level of protection, control, and scalability.
Below are the most important factors to consider, along with practical examples from real-world scenarios.
5.1. Define Your Use Case
Start by asking yourself: Who is the firewall for?
- Home users may need basic filtering, parental controls, and malware protection.
- Small businesses might require access logs, bandwidth management, and limited VPN.
- Large organizations need advanced threat prevention, centralized management, and scalability.
When consulting for a coworking space, I found a cloud-managed firewall ideal—it allowed remote rule updates and bandwidth reports without needing on-site IT.
5.2. Match Firewall Type to Your Needs
Refer back to Section 3 to determine whether you need:
- Packet-filtering for low-latency filtering
- Stateful inspection for active session control
- Proxy for application-layer filtering
- NGFW for comprehensive protection (recommended for businesses)
- Hardware/software/cloud-based depending on infrastructure
5.3. Consider Features You Really Need
Not all firewalls come with the same toolset. Here are must-haves based on environment:
| Environment | Essential Features |
|---|---|
| Home | Basic filtering, malware blocking, DoH |
| Remote work | VPN support, app control, remote updates |
| Office | Stateful inspection, intrusion detection |
| Enterprise | NGFW, sandboxing, SSL inspection, logging |
Tip: Avoid overpaying for features you won’t use. Choose scalability over complexity.
5.4. Ease of Use and Interface
If the firewall is difficult to configure or monitor, it won’t be used effectively.
Look for:
- Intuitive dashboard
- Visual traffic charts
- Rule templates and preset modes (e.g., “Office”, “Home”, “DMZ”)
- Vendor support and documentation
One client initially chose an advanced NGFW but couldn’t manage it. Switching to a more user-friendly model solved deployment issues.
5.5. Budget and Licensing Model
Firewall solutions range from free (open-source software) to thousands of dollars annually (NGFWs with subscriptions).
Evaluate:
-
Upfront hardware/software cost
-
Ongoing maintenance and support fees
-
Licensing limits (number of users, devices, or throughput)
5.6. Scalability and Future-Proofing
Networks grow. Choose a firewall that can scale with:
-
More users or devices
-
Increased bandwidth
-
New locations (multi-site or cloud integrations)
-
Advanced security threats
Look for modular firewalls or those with upgrade paths.
6. Best Practices for Firewall Implementation
To get the most out of your firewall:
-
Regularly update firmware and patch vulnerabilities
-
Log traffic and monitor for irregular patterns
-
Back up configurations and test failover scenarios
-
Create tailored rules—avoid “allow all” defaults
-
Perform periodic security audits
These steps strengthen your firewall and reduce risk exposure.

7. Conclusion
Understanding what is a firewall and how it functions is no longer optional—it’s a must-have knowledge in the digital age. Firewalls are the digital gatekeepers of your network, filtering harmful traffic while allowing legitimate access.
Whether you’re a casual user or a system administrator, taking the time to configure a proper firewall setup could save you from serious cyber threats down the line.
For more expert tips and real-world guides, visit the Networking section at Softbuzz.