What Is BitLocker Encryption?
It’s Windows’ built-in encryption tool that protects your data by locking entire drives with a password, PIN, or hardware chip—so no one can read your files without your permission.
I used to travel with my work laptop every day—until one morning I left it on a train. Panic set in. My files? Client contracts? Gone, I thought.
But thanks to BitLocker encryption, not a single byte was exposed. My drive was completely locked—scrambled into unreadable code. That moment made me realize how critical this feature is.
So, what is BitLocker encryption? In simple terms, it’s Microsoft’s built-in tool for locking down your drives—transforming your files into secure, inaccessible data unless the right PIN, password, or chip unlocks it.
In 2025, as remote work surges and privacy laws tighten, BitLocker is no longer optional—it’s essential. Whether you’re protecting sensitive business files or family photos, this guide will show you how BitLocker works, why it matters, and how to enable it in minutes.
What Is BitLocker Encryption?
BitLocker encryption is Microsoft’s built-in data protection tool for Windows, designed to secure your files by encrypting entire drives—whether internal or removable. Once enabled, it transforms your data into unreadable code that can’t be accessed without the correct password, PIN, or recovery key.
Available in Windows 10/11 Pro, Enterprise, and Education editions, BitLocker primarily protects three types of storage:
-
System drives (your C: drive)
-
Fixed data drives (internal storage not containing the OS)
-
Removable drives (USBs, via BitLocker To Go)

What is BitLocker Encryption
Key Highlights:
-
Core purpose: Encrypt data at rest to protect against unauthorized access
-
Applies to: HDDs, SSDs, USB flash drives
-
Use cases: Device theft, loss, compliance with privacy regulations
Real-life story: I learned the true value of BitLocker the hard way—my laptop was stolen at a conference in 2023. Luckily, I had BitLocker enabled. The thief walked away with hardware, but my client contracts, financials, and personal notes remained completely inaccessible. Without the decryption key, the drive was just encrypted gibberish.
Why BitLocker Matters in 2025
In today’s climate of data breaches, remote work, and tightened regulations like GDPR and HIPAA, losing a device doesn’t just mean losing hardware—it can mean exposing personal or professional information. BitLocker encryption ensures that even if your device ends up in the wrong hands, your data stays protected.
Definition Snapshot (for Featured Snippet):
BitLocker encryption is a Windows security feature that locks data on drives using strong encryption (AES-128 or AES-256), making it unreadable without proper authentication.
This encryption happens transparently in the background, so you don’t have to manually encrypt files one-by-one. Once set up, it works silently—protecting your privacy without slowing down your workflow.
How Does BitLocker Work? (Beginner-Friendly)
BitLocker encryption works by converting your drive’s data into encrypted code that can only be “unlocked” using a secure authentication method—like a PIN, password, or Trusted Platform Module (TPM). This ensures that unauthorized users can’t read your files, even if they physically remove the hard drive and plug it into another device.
Here’s how BitLocker functions behind the scenes:
BitLocker Authentication Process:
-
Device powers on
-
BitLocker prompts for authentication (PIN, password, or TPM check)
-
If verified, the system decrypts data in real-time—giving you full access
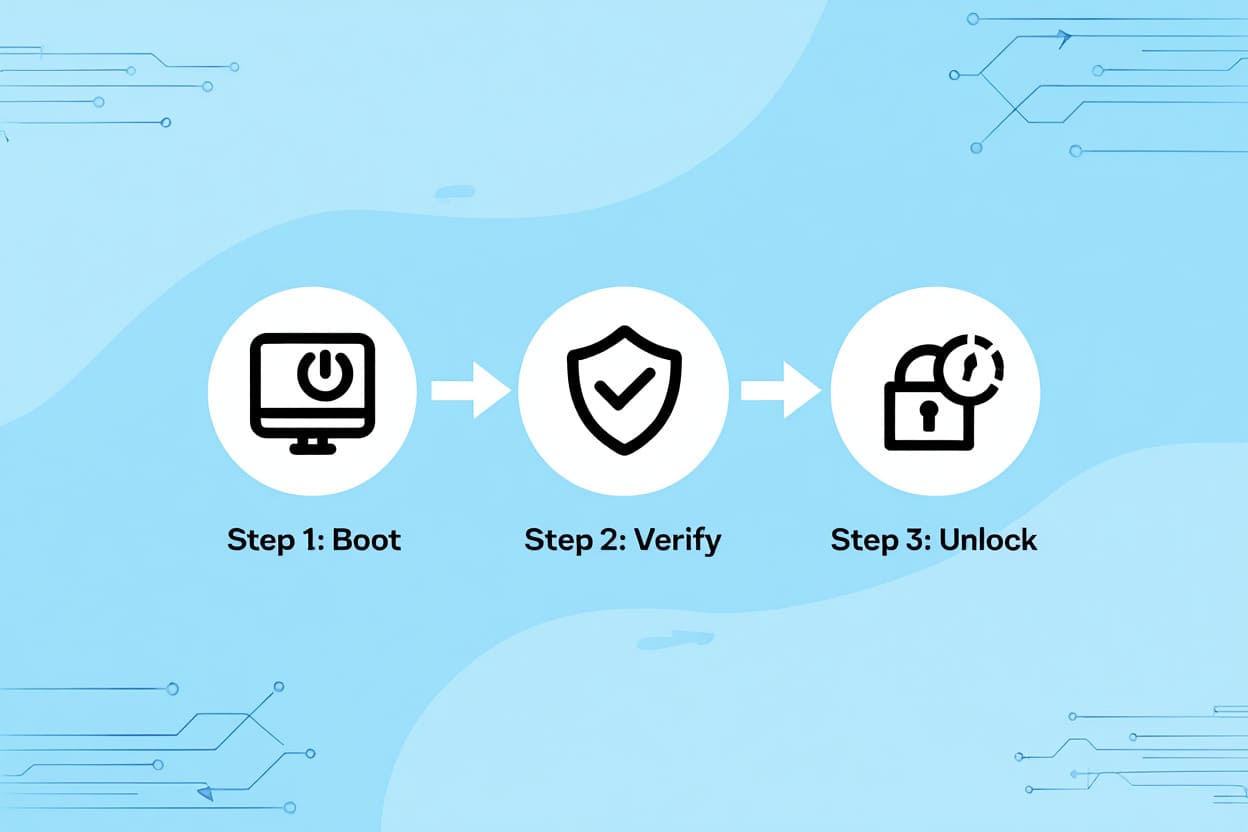
How BitLocker Works
All of this happens without slowing down your computer or requiring constant user input.
Personal experience: I once had to recover data from a colleague’s encrypted laptop after he left it behind on a flight. Without his BitLocker recovery key, it was impossible to access—even with admin tools. That’s when I realized: BitLocker doesn’t just secure—it locks down like a vault.
Local Encryption = Real Protection
BitLocker doesn’t send any data to the cloud. Instead, it stores encrypted credentials locally in the TPM chip, a secure hardware component soldered onto most modern Windows PCs. This setup offers several key benefits:
-
On-the-fly encryption: You can work normally; the system handles encryption/decryption in real time.
-
Failsafe access: Forgot your PIN? Use your saved recovery key to regain access.
-
Hardware-level trust: TPM ensures that keys can’t be tampered with—even if attackers pull out the hard drive.
Tip: You can check if your device supports BitLocker and TPM by typing tpm.msc into the Windows Run box (Win + R).
Whether you’re encrypting a business laptop or a USB drive with BitLocker To Go, the result is the same: strong, seamless, and secure access for you—nothing but encrypted gibberish for everyone else.
Why Use BitLocker? (Benefits, Risks, and Limitations)
BitLocker encryption is more than just a tech feature—it’s a critical defense layer in an era where data breaches and regulatory fines can cost millions. If you’re managing confidential files or handling client data, enabling BitLocker in 2025 is no longer optional—it’s essential.
Top Benefits of BitLocker
-
Strong Data Protection: Encrypts your entire drive, preventing unauthorized access even if the device is lost or stolen.
-
Regulatory Compliance: Helps meet strict standards like GDPR, HIPAA, and PCI-DSS, reducing legal and financial risks.
-
User-Friendly: Integrated into Windows Pro, Enterprise, and Education—no need for third-party software or steep learning curves.
-
Cost-Effective: Included with Windows; no extra licensing required for most users.
-
Peace of Mind: Knowing your sensitive documents, photos, and business records are protected—even when offline.

Real-Life BitLocker Use Cases
Real-life example: When my external SSD went missing during a work trip, I didn’t panic. Thanks to BitLocker To Go, I knew the files inside were unreadable without the recovery key—no matter who found it.
BitLocker: Advantages vs. Limitations
| Advantages | Limitations |
|---|---|
| Seamless Windows integration | Only protects data at rest—not against malware or live attacks |
| Supports USB encryption via BitLocker To Go | Requires TPM for strongest security (not all devices have it) |
| Allows automated key backups (e.g., Microsoft account, Active Directory) | Not available on Windows Home editions |
Use Cases Where BitLocker Shines
-
Remote Work Security: Encrypt company laptops issued to remote employees
-
Healthcare & Legal: Protect sensitive client and patient records
-
Enterprise Risk Management: Prevent data leaks from insider threats or stolen hardware
-
Education: Secure student data and staff laptops in compliance with FERPA
Tip: If you operate in a regulated industry, enabling BitLocker is often a quick win to pass security audits.
BitLocker Features & Options in 2025: What You Can Do
In 2025, BitLocker encryption has evolved into a full-fledged data protection suite with advanced features, enabling both individual users and IT administrators to safeguard sensitive information with greater flexibility and control.
Whether you’re encrypting a personal laptop or deploying policies across an enterprise network, BitLocker offers a robust set of tools tailored to today’s cybersecurity demands.
Key Features of BitLocker:
-
Full-Disk Encryption: Automatically encrypts the entire drive, securing operating system files, documents, and temporary data against unauthorized access.
-
BitLocker To Go: Extends protection to USB flash drives and other portable storage, ensuring data stays encrypted even when disconnected from your primary device.
-
Flexible Authentication Methods: Supports PINs, passwords, and hardware-backed protection via TPM (Trusted Platform Module), enhancing identity verification.
-
AES Encryption Standards: Uses AES-128 or AES-256 encryption in XTS mode, meeting industry benchmarks for cryptographic strength.
-
Recovery Key Management: Recovery keys can be safely backed up to a Microsoft account, Active Directory, or saved offline—critical for emergency data access.
-
Group Policy & Intune Support: IT administrators can enforce encryption standards, manage keys, and monitor compliance using centralized tools.
-
Network Unlock (Enterprise): Allows devices connected to a trusted corporate network to boot securely without user intervention, improving remote work productivity.
These BitLocker features combine usability and security, making it easier than ever to protect data at rest without slowing down your device or compromising workflow.
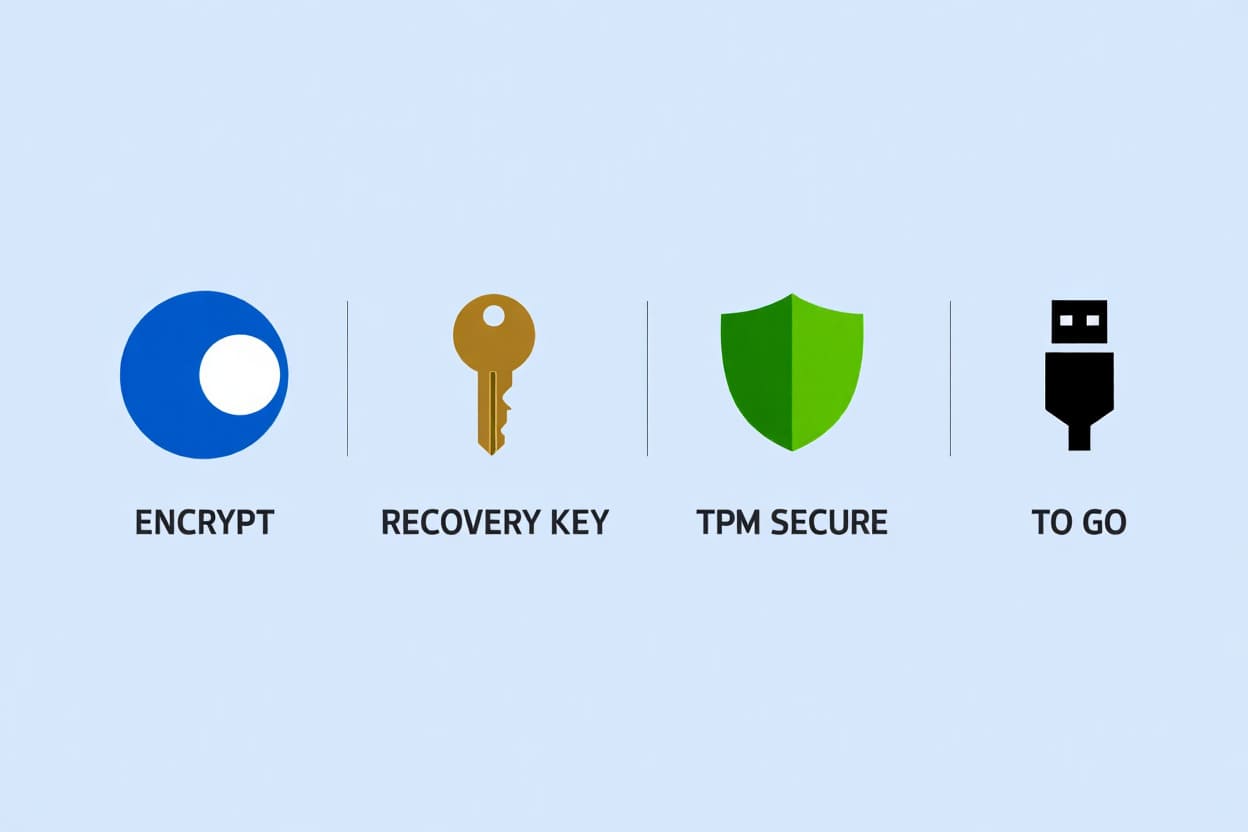
BitLocker Features in 2025
Pro Tip: For removable media, BitLocker To Go provides peace of mind when sharing files across different locations—especially in industries where USB data leakage poses compliance risks.
If you’re still exploring your encryption options or wondering how BitLocker compares to open-source alternatives, don’t miss our full comparison in the section “How Does BitLocker Compare to Other Encryption Solutions?”
How to Use BitLocker: Step-by-Step Basics
Activating BitLocker is straightforward on supported Windows versions such as Pro, Enterprise, and Education editions.
Supported Windows Versions:
- Windows 10 Pro, Enterprise, Education
- Windows 11 Pro, Enterprise, Education
Steps to Enable BitLocker:
- Open the Control Panel and navigate to “BitLocker Drive Encryption.”
- Choose the drive you want to encrypt and click “Turn on BitLocker.”
- Select an unlock method (password, PIN, TPM).
- Save or print your recovery key in a safe location—this key is critical to regain access if you forget your credentials.
- Choose encryption options (encrypt used disk space only or the entire drive).
- Start the encryption process; your drive will be secured in the background.
During setup, the system provides clear prompts and status indicators, making the process accessible even for non-technical users.
BitLocker Data Recovery & Troubleshooting
Losing your BitLocker password or recovery key can be stressful, but there are established solutions.
What To Do If You Lose Your Credentials:
- Check if your recovery key is saved to your Microsoft account (accessible via Microsoft website).
- Look for any printed or USB-drive backups of the recovery key.
- Consult your organization’s IT department if managed centrally.
Common Problems and Fixes:
- Drive not unlocking: Verify correct password or recovery key; if TPM is used, ensure BIOS/firmware settings haven’t changed.
- BitLocker lockout: Use recovery key prompt provided at boot.
BitLocker’s recovery interface guides the user through safe steps to regain access without risking data loss.
BitLocker Security, Privacy, and Compliance in 2025
BitLocker encryption in 2025 remains a cornerstone of Windows-based data protection strategies, built on robust security protocols and global compliance alignment. It utilizes Advanced Encryption Standard (AES) with configurable 128-bit or 256-bit keys, securing data at rest with industry-recognized cryptographic strength.
Security Mechanisms That Build Trust:
-
TPM Integration: BitLocker stores encryption keys in the Trusted Platform Module (TPM), a secure hardware chip, shielding credentials from software-based attacks.
-
XTS-AES Mode: Ensures stronger integrity protection for disk sectors and guards against common cryptographic vulnerabilities.
-
Automatic Lockout: Repeated failed attempts trigger access lockouts, mitigating brute-force and physical tampering risks.
-
Local Authentication: Since decryption keys never leave the device, BitLocker significantly reduces the attack surface compared to cloud-managed solutions.
Privacy Assurance:
Unlike some third-party tools, BitLocker does not transmit data or keys to Microsoft. All encryption and verification are performed locally, helping organizations meet strict data sovereignty and privacy regulations.
Compliance with Global Standards:
In 2025, BitLocker helps businesses and institutions comply with:
-
GDPR (EU)
-
HIPAA (US Healthcare)
-
PCI DSS (Payment card industry)
-
ISO/IEC 27001 and emerging local frameworks in Asia-Pacific and LATAM regions
These alignments make BitLocker an attractive option for enterprises handling sensitive personal, financial, or healthcare data.
Insight: A 2024 IDC survey found that over 70% of Windows-based enterprises use BitLocker to satisfy encryption mandates—a number projected to rise as zero-trust frameworks and remote work persist.
When used as part of a layered defense strategy, BitLocker plays a pivotal role in achieving zero-compromise data security in the modern enterprise. To boost your endpoint protection even further, see our guide on what is a firewall.
How Does BitLocker Compare to Other Encryption Solutions?
If you’re choosing an encryption tool in 2025, comparing BitLocker with options like VeraCrypt, FileVault (macOS), and others is key to finding the right fit for your privacy and platform needs.
Comparative Overview
| Feature | BitLocker | VeraCrypt | FileVault (macOS) | Third-Party Tools |
|---|---|---|---|---|
| Platform Support | Windows Pro, Enterprise, Education | Windows, Linux, macOS | macOS only | Varies (Windows/macOS/Linux) |
| Ease of Use | Built-in, user-friendly | Technical setup required | Seamless for macOS users | Depends on provider |
| Security | AES 128/256 with TPM-based storage | Advanced encryption algorithms | AES 256 with hardware acceleration | Varies (often lacks TPM support) |
| Cost | Free with Windows editions | Free, open-source | Free with macOS | Usually paid |
| Compliance | Meets GDPR, HIPAA, PCI DSS | User-configured (not standardized) | Meets Apple security standards | Varies (not always compliant) |
Why BitLocker Often Wins in Enterprise Environments
For businesses and professionals using Windows, BitLocker stands out due to its:
-
Seamless integration with Windows Security and Group Policy
-
Support for enterprise encryption policies and Active Directory
-
TPM-based protection, which enhances hardware-level security
-
Centralized recovery key management using Microsoft tools
When to Consider Alternatives
-
VeraCrypt: Ideal for tech-savvy users who need full control, especially on Linux or dual-boot systems. It’s open source and highly customizable but lacks built-in enterprise support.
-
FileVault: Best for macOS users seeking Apple-native encryption. It integrates effortlessly with macOS but doesn’t support Windows or Linux.
-
Third-Party Encryption Tools: These vary in quality. Some offer cross-platform support or added cloud features, but few match BitLocker’s security and compliance for enterprise-grade use.
Author’s Note: As someone managing a hybrid Windows/macOS IT environment, I’ve consistently relied on BitLocker for ease of rollout and policy enforcement across 100+ endpoints—something harder to scale with open-source or non-native tools.
Frequently Asked Questions About BitLocker
Q1: Will BitLocker slow down my PC?
A: No. BitLocker is optimized for performance and uses hardware acceleration when available. Most users report minimal to no impact on system speed, especially with modern SSDs and TPM 2.0 chips.
Q2: Can I use BitLocker on USB drives?
A: Yes. BitLocker To Go is a feature specifically designed to encrypt USB flash drives and other removable storage, ensuring your data remains secure even when transferred between devices.
Q3: Can Microsoft recover my lost BitLocker key?
A: Only if you saved your recovery key to your Microsoft account. If not, recovery depends on whether you’ve backed it up manually—printed copy, USB storage, or corporate IT management.
Q4: Do I need special hardware to use BitLocker?
A: A TPM chip is recommended for best security and seamless operation, but BitLocker can also function with a password or USB startup key on systems without TPM.
Q5: Is BitLocker safe to use?
A: Yes. BitLocker leverages industry-standard AES encryption (128- or 256-bit) and is widely trusted by global enterprises for protecting data at rest.
Q6: Is BitLocker available on Windows Home editions?
A: No. BitLocker is only included with Windows Pro, Enterprise, and Education editions. Windows Home users must upgrade to access full encryption features.
Q7: Does BitLocker protect against hackers or viruses?
A: BitLocker protects data at rest. While it won’t stop malware once a system is running, it prevents data theft if your device is lost, stolen, or accessed without authorization.
Q8: What’s the difference between BitLocker and BitLocker To Go?
A: BitLocker encrypts fixed internal system and data drives. BitLocker To Go extends this protection to external storage like USB flash drives and portable hard disks.
Q9: Can BitLocker be disabled?
A: Yes, you can suspend or disable BitLocker via the Windows settings. However, doing so exposes your data, so it’s advised only in trusted, temporary circumstances. Always back up recovery keys before making changes.
30+ BitLocker Checklist: Secure Setup and Best Practices for 2025
After years of using BitLocker in enterprise environments, I built this checklist to help you secure data effectively—without the usual setup headaches.
BitLocker Setup & Security Checklist
Setup:
- Ensure device runs compatible Windows Pro, Enterprise, or Education.
- Update to the latest Windows security patches before enabling.
- Verify presence and functionality of TPM chip if available.
- Backup all personal files before starting encryption.
- Choose between password, PIN, or hardware-based unlock method appropriately.
- Select AES 128-bit or 256-bit encryption strength based on security needs.
Recovery:
- Save recovery key securely—not on the encrypted drive itself.
- Print a physical copy of the recovery key and store it safely offline.
- Back up recovery key in multiple secure locations (personal vault, cloud with encryption, Microsoft account).
- Test recovery key validity before relying on BitLocker encryption fully.
Backup recovery key in multiple secure locations (personal vault, encrypted cloud services, Microsoft account). For more protection, you can also explore what is cloud backup to understand how to store keys securely off-device.
Management & Compliance:
- Use BitLocker To Go for encrypting USB and removable drives.
- Enable auto-unlock only for trusted devices.
- Implement Group Policy to enforce encryption policies in corporate settings.
- Restrict who can disable or suspend BitLocker in your organization.
- Audit and document all recovery key holders.
Ongoing Care:
- Encrypt all drives, not just the system partition.
- Use BitLocker Network Unlock for managed enterprise devices.
- Regularly audit BitLocker status via Windows Security Center.
- Train users on BitLocker basics, recovery procedures, and security best practices.
- Avoid storing recovery keys in cloud drives without additional encryption.
- Monitor BitLocker prompts after major Windows updates.
- Use device passwords or PINs even when TPM is present.
- Review BitLocker logs to catch issues early.
- Keep BitLocker active when selling or donating devices; otherwise, securely wipe data.
- Verify compatibility with third-party security software to avoid conflicts.
- Confirm BitLocker support after major Windows feature upgrades.
- Whenever possible, use two-factor authentication as an added layer of security.
Conclusion
What is BitLocker encryption? In 2025, it’s not just a Windows feature—it’s a critical tool for protecting your personal and business data against loss, theft, and unauthorized access. By encrypting entire drives and storing keys securely with TPM, BitLocker offers:
-
End-to-end drive protection for laptops, desktops, and USBs
-
Seamless integration into Windows Pro, Enterprise, and Education
-
Compliance with top security standards like GDPR, HIPAA, and PCI DSS
-
Practical ease-of-use with robust recovery and management options
Whether you’re an individual seeking peace of mind or an IT admin enforcing organization-wide compliance, BitLocker makes modern data security accessible and effective.
For more in-depth guides on securing Windows devices, visit our Windows category. And don’t forget to check out Softbuzz.net for more trusted tech insights and helpful tutorials.










