User Account Control (UAC) is a built-in Windows security feature that stops unauthorized changes by requiring user approval before apps can make system-level modifications.
In early 2025, I downloaded a utility tool from what I thought was a trusted site. Just before installation, a UAC prompt popped up—warning me that the app was unverified. That one prompt saved my PC from a hidden malware payload. Since then, I’ve seen UAC as more than a popup—it’s a real-time safety net.
In this guide, you’ll learn exactly what UAC in Windows is, how it works behind the scenes, how to adjust its settings, and why it’s a key part of your PC’s defense system in 2025.
What is UAC in Windows? (Updated for 2025 Security Standards)
User Account Control (UAC) in Windows is a built-in security feature designed to protect your system from unauthorized changes and malware attacks. So, what is UAC in Windows exactly? It’s a real-time access management layer that requires users to confirm or deny system-level operations—like installing software or modifying critical settings—before they’re allowed to proceed.
First introduced in Windows Vista, UAC was Microsoft’s response to the growing need for stricter control over administrative privileges. In 2025, it remains an essential part of Windows’ multi-layered security strategy.

What is UAC in Windows
Core functions of User Account Control include:
-
Blocking unauthorized installations or system modifications
-
Prompting users before granting elevated permissions
-
Limiting background malware activity without user consent
-
Enforcing the “least privilege” model for standard user accounts
In simple terms, think of UAC as a vigilant digital gatekeeper. Every time an app tries to make system-level changes, UAC steps in—asking for your explicit permission. This helps protect your device from unintended disruptions and silent malware execution, keeping your Windows environment secure and user-controlled.
How Does UAC Work in Windows?
To truly understand what UAC in Windows is, you need to see how it functions behind the scenes. User Account Control (UAC) kicks in anytime an action could affect system integrity—like installing new apps, modifying core settings, or changing device drivers.
Here’s a simplified breakdown of how UAC works in real time:
-
Trigger: You launch a task that requires administrative privileges (e.g., installing Zoom).
-
Secure Prompt Appears: Windows dims the screen (Secure Desktop) and shows a UAC dialog asking for your consent.
-
Details Provided: The prompt displays the app name, publisher, and permission request.
-
User Decision: Click Yes to proceed or No to deny the action.
-
Role-Based Behavior:
-
Standard users must enter an admin password.
-
Admin users just confirm the action with a click.
-
Example: When I installed Zoom on my home PC, UAC asked, “Do you want to allow this app to make changes to your device?” That pause reminded me I was still in control—no silent installs, no backdoor tricks.
This mechanism ensures Windows users remain the gatekeepers of their own systems, blocking changes unless explicitly approved.
Why Does UAC Exist? Security Benefits Explained
To understand what is UAC in Windows, you need to grasp its purpose: limiting administrative privileges to reduce security risks. Microsoft introduced User Account Control (UAC) to prevent unauthorized changes, especially those made silently by malware or careless user actions.
Here are the top security benefits of UAC in 2025:
-
Prevents accidental system changes: By prompting before critical actions, UAC stops users or apps from unintentionally modifying essential settings or files.
-
Blocks malware privilege escalation: Malware often seeks to run with admin rights. UAC creates a critical barrier that blocks these silent takeovers.
-
Enforces the principle of least privilege: Users operate under standard permissions, and elevation is requested only when necessary—minimizing risk exposure.
-
Strengthens layered security: UAC complements Windows Defender, Firewall, and SmartScreen, forming a multi-layered protection strategy against modern cyber threats. For a closer look at how the firewall layer works alongside UAC, check out our full guide on What is Windows Defender Firewall.
Real-World Impact
In real-world attacks—including ransomware and backdoor malware—UAC has proven effective in halting unauthorized system access before damage is done. It provides a valuable pause for users to evaluate each elevated request, reducing the success rate of social engineering or zero-click malware installations.
In summary, what is UAC in Windows if not a gatekeeper? It’s a vital part of Windows’ security ecosystem, giving users control and reducing the attack surface by design.
UAC in Everyday Usage: What Windows Users Experience in 2025
What is UAC in Windows, and why is it still so important in 2025? User Account Control (UAC) was designed to prevent unauthorized changes to your system by enforcing least-privilege access—a key concept in modern cybersecurity.
Here’s how UAC directly benefits everyday users:
-
Prevents unintended system changes: UAC stops unauthorized apps or users from altering critical settings without your explicit approval.
-
Blocks malware privilege escalation: Even if malware enters your system, UAC stops it from gaining admin access without your consent.
-
Encourages least-privilege computing: Everyday accounts operate with limited rights. UAC only elevates access when absolutely necessary.
-
Enhances layered protection: UAC works seamlessly with Windows Defender, Firewall, and SmartScreen to form a multi-layered defense strategy.
Real-World Example
In one case, a user unknowingly downloaded a malicious file disguised as a utility tool. UAC’s prompt halted the program from executing with administrator privileges. That simple notification prevented system-wide compromise—giving time for antivirus tools to detect and remove the threat.
In short, what is UAC in Windows if not your first alert system against unauthorized actions? It keeps users informed, involved, and protected—making it essential for safe computing in both home and enterprise environments.
UAC Levels and Customization: Windows Settings Explained (2025)
A key part of understanding what UAC in Windows truly is lies in how flexible it has become. In Windows 11 and 2025 builds, User Account Control (UAC) offers four customizable notification levels, giving users the power to fine-tune the balance between security and convenience.
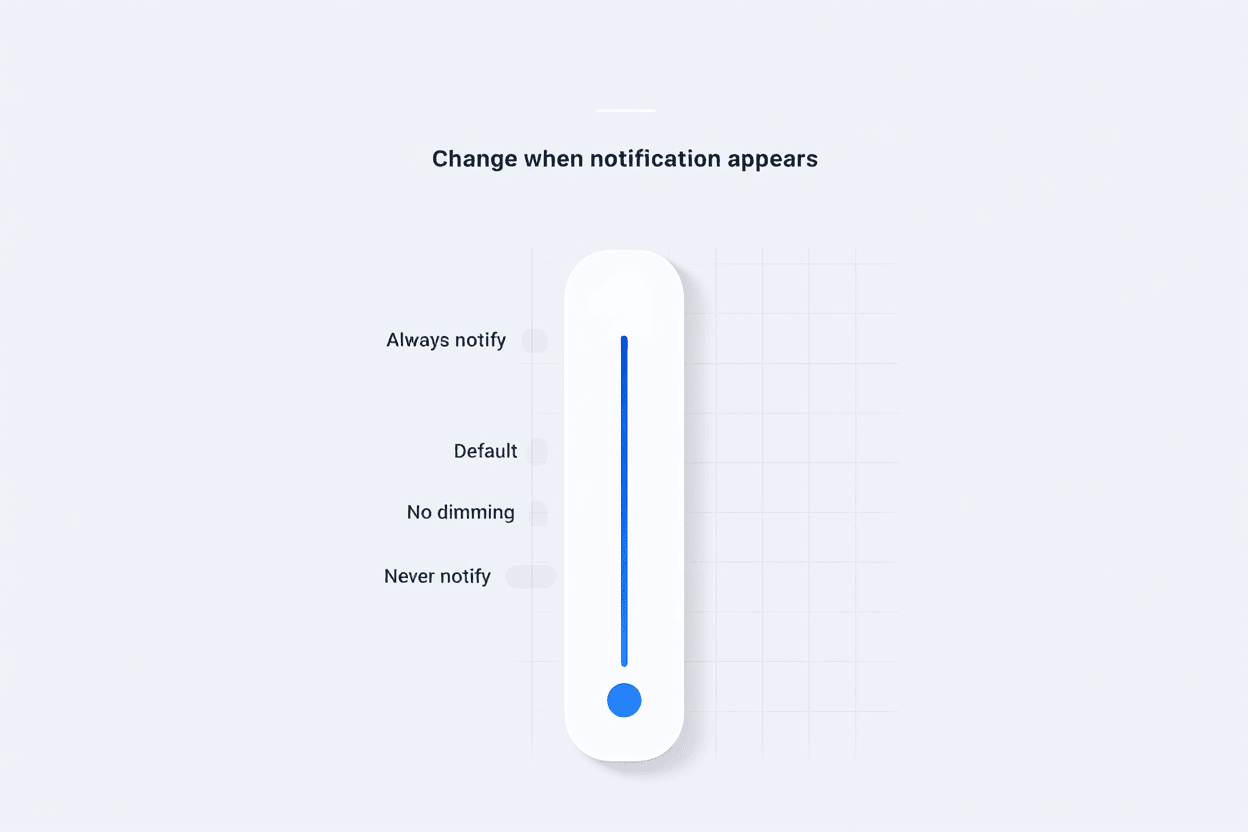
UAC settings levels in Windows 11/2025
UAC Notification Levels
-
Always notify
-
Prompts whenever any system-level or app change is attempted.
-
Best for high-security environments or IT admins.
-
-
Notify only when apps try to make changes (Default)
-
Alerts you to app-initiated changes but skips notifications for user-driven actions.
-
Ideal for most users and family PCs.
-
-
Notify only when apps try changes (no dimming)
-
Same behavior as the default, but skips Secure Desktop dimming.
-
More visually fluid, slightly less secure.
-
-
Never notify
-
Disables UAC prompts entirely—strongly discouraged unless in test environments.
-
How to Change UAC Settings in Windows 11/2025
-
Open Control Panel or search “UAC” in the Start menu.
-
Click “Change User Account Control settings.”
-
Adjust the slider to your preferred notification level.
-
Click OK (Admin approval required).
Expert Tip: If you’re an advanced user or developer, consider using Group Policy Editor to set enterprise-wide rules, enforce Secure Desktop mode, or log elevation attempts.
Security Reminder: Lowering UAC sensitivity can expose your system to hidden privilege escalations. If you reduce notifications, be sure to pair it with a strong antivirus, SmartScreen, and secure software practices.
UAC vs. Other Windows Security Features: How They Work Together
To fully understand what is UAC in Windows, it’s important to compare it with other native Windows security tools. Each serves a specific role, but they complement one another in a layered protection strategy.
Here’s how User Account Control (UAC) compares with other key Windows security features:
| Feature | Blocks Malware | Prevents Unauthorized Changes | Requires User Confirmation | Example Use Case |
|---|---|---|---|---|
| User Account Control (UAC) | No | Yes | Yes | Prompt when installing software |
| Windows Defender | Yes | No | No | Scans for and removes malware |
| Windows Firewall | Yes | No | No | Blocks suspicious inbound/outbound traffic |
| SmartScreen Filter | Yes | No | No | Warns users before opening risky downloads |
Comparison of UAC with other Windows security tools
While Windows Defender and Firewall work quietly in the background, UAC adds a crucial user-driven layer. It prompts you before system-level changes, stopping malware or unauthorized apps from acting without your consent.
That’s why when people ask what is UAC in Windows, the best answer is this: it’s a proactive checkpoint that empowers users while complementing Windows’ automated defenses.
Advanced UAC Insights for IT Pros and Power Users
For system administrators and tech-savvy users, mastering how User Account Control (UAC) works under the hood is essential to maintaining secure and efficient Windows environments in 2025.
- Permissions and escalation: UAC uses two access tokens—one with standard user rights and one with full administrator rights. Elevation occurs when explicit consent is granted. The Secure Desktop mode isolates the prompt from other processes to prevent spoofing.
- Domain and enterprise management: UAC settings can be centrally controlled through Group Policy, enabling organizations to enforce uniform security policies and customize behavior per department or role.
- Troubleshooting: Common issues include denied elevation due to corrupted tokens or blocked silent installations. Solutions involve registry edits, adjusting compatibility settings, or scripting elevation requests. If you’re not familiar with editing the Windows registry, we recommend reading What is Registry Editor to understand how it works and how to avoid critical mistakes.
- Best practices: Maximize security by enforcing least privilege, regularly auditing UAC event logs, and educating users about recognizing legitimate prompts.
Scripts for automating elevation requests or registry tweaks for tailored configurations are common in advanced environments, facilitating smoother workflows while maintaining tight security controls.
Common Misconceptions and Frequently Asked Questions About UAC
Q1: Is it safe to turn off UAC?
A1: Generally, no. Disabling User Account Control (UAC) removes a key layer of defense, increasing the risk of malware and unauthorized system changes. It’s only advisable in tightly managed test environments with strong alternative security measures in place.
Q2: Why does UAC pop up so much?
A2: Frequent UAC prompts usually stem from apps that repeatedly request elevated permissions or from frequent system configuration changes. Keeping software updated and adjusting UAC notification levels can help reduce these interruptions without disabling security.
Q3: Does UAC replace antivirus software?
A3: No. UAC is not a replacement for antivirus protection. It provides a safeguard by requiring user consent before system-level actions, but it does not detect or remove threats like Windows Defender or third-party antivirus programs do.
Q4: Can I bypass UAC prompts safely?
A4: Bypassing UAC is strongly discouraged. Doing so can expose your system to elevated risks from unauthorized actions and malware. Legitimate elevation should always be confirmed manually for safe operation.
Q5: Why use UAC if I already have Windows Defender and Firewall?
A5: UAC adds user-controlled verification to system-level actions, unlike Defender or Firewall, which work automatically in the background. This manual layer of control helps catch potentially risky changes before they’re allowed to proceed.
Conclusion
What is UAC in Windows? It’s more than just a popup—it’s your system’s first line of defense against unauthorized changes and hidden malware threats. Whether you’re a casual user or a seasoned IT admin, mastering how User Account Control works will give you more control, fewer risks, and a cleaner digital experience.
Let’s recap what makes UAC so important:
-
Prevents malware from silently making system-level changes
-
Reinforces the principle of least privilege for safer computing
-
Adds a vital security layer to modern Windows environments
If you’re passionate about fine-tuning your PC or diving deeper into Windows features, don’t miss our curated insights in the Windows Tips & Tricks category—a must-read for tech-savvy users like you.
Still hungry for more expert-backed tips? Visit the Softbuzz homepage to explore our latest tutorials, reviews, and performance guides tailored for power users and beginners alike.









